Since 2017, APT3 has been tested and analyzed by MITRE for use as test data. In ATT&CK VIEW, released fall of 2018, MITRE suggests a plan for the emulation of the APT3 attack plan. In the following post, the known attack techniques used by the APT3 group will be explained with matches to the MITRE Technique numbers (Txxxx), and it will be reproduced primarily with CHEIRON.
At MITRE, APT3 is given the ID G0022, and it is also called Gothic Panda, Pirpi, UPS Team, Buckeye, Threat Group-0110, and TG-0110. In particular, the group was discovered to have a strong supporter in China’s Ministry of State Security and has relations with infamous hacking campaigns, including Operation Clandestine Fox, Operation Clandestine Wolf, and Operation Double Tap. In 2015, the group was found to have attacked America and even extended attacks to Hong Kong’s leading political group at the time.
APT3 Attack Analysis
The 3 phases of APT3 attacks analyzed by MITRE are shown in the image below. The first phase is the initial infection, the second phase is network spread, and the final phase is information leaking.
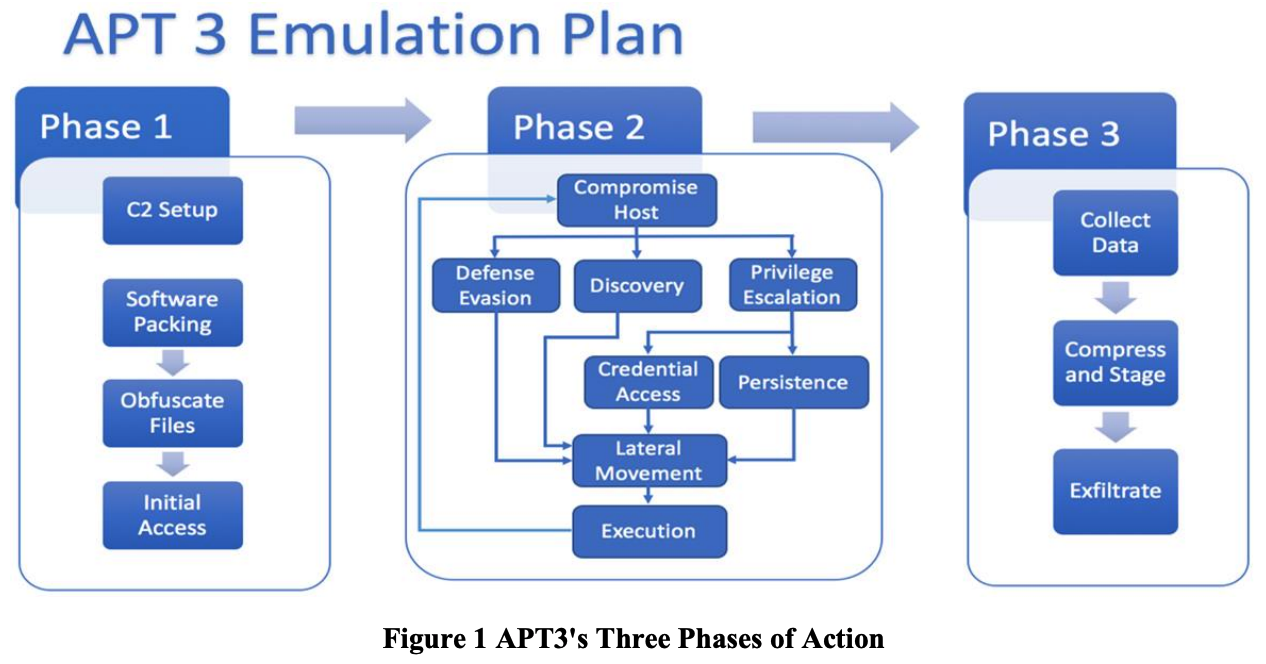
Image - APT3 3 Attack Phases (Mitre)
Attack 1st Phase - Initial Infection
Through the analysis of 5 cases, the initial infection techniques have been analyzed and compiled. Ultimately, via a weakness or social engineering, the Pirpi or PlugX malicious code is installed.
1. IE CVE-2014-6332
-
A link that redirects to a malicious site is spread via a spear phishing scam
-
The malicious site exploits the CVE-2014-6332 weakness that allows the execution of Powershell and VBScript
-
The Powershell downloads and runs the install.exe file and drops the two test.exe and doc.exe files into the local system channel (In Windows XP C:\Users\Public path does not exist so the attack fails)
-
In 2014, text.exe and a file with similar principles called ‘Pirpi’ are downloaded
- T1068 - Exploit Vulnerability doc.exe uses CVE-2014-4113 (Windows Kernel Exploit) to gain system control and uses that control to execute test.exe
- Running text.exe results in:
- T1033 - System Owner/User Discovery / T1059 - Command-Line Interface (Identifying the admin with the below command)
cmd.exe /c whoami
-
T1053 - Scehduled Task using the schtasks command inserts into the scheduler an execution to make test.exe the system administrator
schtasks /create /tn "mysc" /tr C:\Users\Public\test.exe /sc ONLOGON /ru "System"3. After text.exe infection: -
Creates 4 files: %temp%\notepad.exe, %temp%\notepad1.exe, %temp%\notepad2.exe, %temp%\newnotepad.exe
-
T1041 Exfiltration Over Command and Control Channel sends the %temp%\note.txt file (expected that the file contains information)
-
T1095 Standard Non-Application Layer Protocol, T1090 Connection Proxy using the SOCKS5 protocol tries to connect to TCP Port 1913 and a particular IP
-
The packet is indicated with 05 01 00, so a verification is made as to whether the server’s response starts with 05 00
-
The functionality of each server response
Command ID Description 00 00 00 Content after command ID is written to: C:\Users\[Username]\AppData\Local\Temp\notepad1.exe 00 00 01 Deletes the files: C:\Users\[Username]\AppData\Local\Temp\notepad.exe, C:\Users\[Username]\AppData\Local\Temp\newnotepad.exe 00 00 02 Malware exits 00 00 03 Malware downloads the URL that follows the command ID. The file is saved to: C:\Users\[Username]\AppData\Local\Temp\notepad.exe 00 00 04 Content after command ID is written to: C:\Users\[Username]\AppData\Local\Temp\notepad2.exe 00 00 05 The files notepad1.exe and notepad2.exe are concatenated together and written to C:\Users\[Username]\AppData\Local\Temp\newnotepad.exe and executed 00 00 06 The contents of the following file is sent to the server: C:\Users\[Username]\AppData\Local\Temp\note.txt 00 00 07 The string following the command ID is executed using "cmd /C" and results are sent to server
2. Windows Shortcut File + RAR
- Between the years 2015~2016, uses zip/rar archive files
- T1023 - Shortcut Modification archive includes a shortcut file with the Internet Explorer logo
- Upon clicking the shortcut file, Pirpi RAT is downloaded
3. mail+RAR (ttcalc.exe)
-
In 2014, disguised as a developer seeking employment, a RAR Archive file is sent via mail that disguises as a developer program, attaching to binary (ttcalc.exe)
- If you run ttcalc.exe:
-
Generate Pirpi at %userprofile%\Application\mt.dat with the name mt.dat
-
Generate a specific batch file at %userprofile%\start menu\program files\startup\vc.bat
-
T1085 - Rundll32’s related batch file is a script that uses rundll32.exe to run mt.dat
@echo off cmd.exe /C start rundll32.exe "C:\Documents and Settings\admin\Application Data\mt.dat" UpdvaMt
-
- If you run ttcalc.exe:
4. mail+RAR (ttcalBAK.exe)
- Using a phising mail, spreads an encrypted Self-Extracting RAR Archive that, when run, drops a binary called ttcalBAK.exe
- If you run ttcalBAK.exe:
- T1073 - DLL Side-Loading’s malignant code PlugX DLL generated at %AllUserProfile%\chrome_frame_helper
- As DLL is loading, run PlugX via DLL Side-Loading
- If you run ttcalBAK.exe:
5. Flash Exploit
- Install Pirpi RAT that uses flash weaknesses (CVE-2014-1776, CVE-2015-3113)
- Additional: PWC Blog, Palo Alto Blog
Attack 2nd Phase - Network Spread
The malignant code RAT installed in the first phase carries out the features listed below. MITRE provides information on techniques (Adversary Emulation Field Manual) related to attack 3nd and 3rd phases with technique numbers for each, explaining how to use them via windows commands, Cobalt Strike, and Metasploit. Following is a concise compilation of attack techniques.
- Discovery
- T1083 Data from Local System - Queries local system for my information
- T1087 Account Discovery - Queries for user account information
- T1082 System Information Discovery - Queries for system information
- T1069 Permission Groups Discovery - Queries for group information on user with special permissions (however, assuming the environment is Active Directory, queries for Domain Admins group information)
- T1016 System Network Configuration Discovery - Queries for System Network Configuration Information
- T1049 System Network Connection Discovery - Queries for System Network Connection Information
- T1135 Network Share Discovery - Queries for System Network Share Discovery Information
- T1018 Remote System Discovery - Queries for Remote System Information (however, in the case of ntlst/dclist, executes query command for the DC list in the designated Domain. If Domain Controller privilege is not available, execution fails)
- T1057 Process Discovery - Queries for System Process Information
- Local Privilege Escalation
- With privilge escalation from APT3, use the CVE-2014-4113 Windows Kernel Exploit
- In the case of using Metasploit in the ATT&CK VIEW plan, use the bypass module
- Moreover, use PowerUp
- The following techniques are applied in this type of attack technique:
- T1088 UAC bypass
- T1068 Exploit Vulnerability
- T1044 File System Permissions Weakness
- T1034 Path Interception
- T1058 Service Registry Permissions Weakness
- T1038 DLL Search Order Hijacking
- Credential Access
- T1003 - Credential Dumping
- Use custom version of pwdump
- Use custom compile version of Mimikatz
- T1081 - Credentials in Files
- Use ChromePass (Program made by Nirsoft)
- Use Lazagne (Open source software )
- T1056 - Use Input Capture Keylogger
- T1027 - Obfuscated Files or Information
- Use a keylogger to collect keyboard input information and save as an encrypted file called thumbcache_96.dbx
- T1003 - Credential Dumping
- Persistence
- T1053 - (Scheduled Task) registers in the scheduler the execution of malignant code
- T1060 - the first entry to ‘run keys’ in Registry Run Keys/Start will place the batch file in the start folder
- T1015 - loads cmd.exe and changes the registry value of Accessibility Features sethc.exe (Sticky Keys Binary)
- T1076 - Remote Desktop Protocol Enable RDP
- T1136 - Creates Account support_388945a0 and adds it to the Local Admin Group
-
Lateral Movement / Remote Copy and Execution the below information is slightly different than that analyzed by MITRE
- T1077 Windows Admin Shares, T1078 Valid Accounts, T1035 Service Execution
- proceeding with a valid account via net use
copy evil.exe \\COMP\ADMIN$\System32\acachsrv.exe sc \\COMP create acachsrv binPath= "C:\Windows\System32\acachsrv.exe" start= auto DisplayName= "DisplayName" sc \\COMP start acachsrv
- proceeding with a valid account via net use
- T1077 Windows Admin Shares, T1078 Valid Accounts, T1035 Service Execution
-
T1105 - Remote File Copy, T1021 - Remote Services
- Using a program by the name RemoteCMD(a similar program to PSEXEC), uses a remote system to, for instance, upload files / generate systems
Attack 3rd Phase - Information Leaking
As it is a concise version of techniques used in information leaking, the following information is slightly different from that analyzed by MITRE
- T1005 Data from Local System Office - grabs documents related to the local systems office, differentiating and collecting them
- T1002 Data Compressed - after dropping the Chinese version of WinRAR, uses it to compress information for leaking
- T1074 Data Staged - data that has been compressed is moved to the ‘Recycle bin’
- T1043 Commonly Used Port Port 443 / HTTPS protocl - using the aforementioned port/protocol sends the compressed data
- Information leaking with self-encrypytion (MITRE)
- T1022 Data Encrypted
- T1048 Exfiltration Over Alternative Protocol
- T1041 Exfiltration Over Command and Control Channel
Attack Simulation using CHEIRON
The following image is a redrawing of the 2nd Attack Phase of MITRE’s 3 APT3 Attack Phases. After compromising the host, the discovery stage changes depending on the privilege acquired; specifically, based on the collected information, the techniques for infiltration and additional malignant code installation into the local system changes. In other words, a wide variety of scenarios can arise. In this attack scenario, based off a collected password hash, another local system is infiltratated and additional malignant code is installed.
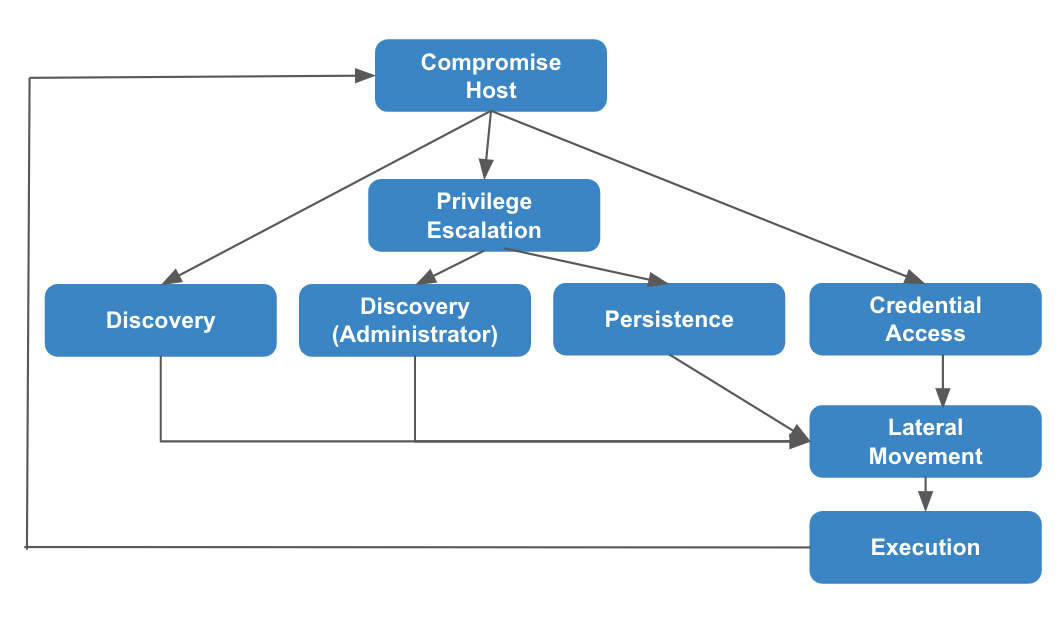
Image - Redrawing of APT3 Attack Phase 2
The following is an integration into CHEIRON of the Attack 2nd Phase Network Spread scenario. Below is a concise version of techniques, but, as listed, are three primary differences from that which was analyzed and tested by MITRE. Described in the image in detail is that which was added or replaced in CHEIRON and anything in grey is not employed in the given scenario. If interested in the image version in English, please contact SOMMA.
- Discovery - divided based on acquired privilege
- Powerup - instead of using Powerup or the Metasploit module, regular windows normal files are used along with generated path tricks to escalate privilege
- Based off the password acquired in Credential Access, execute the Pass the hash attack technique
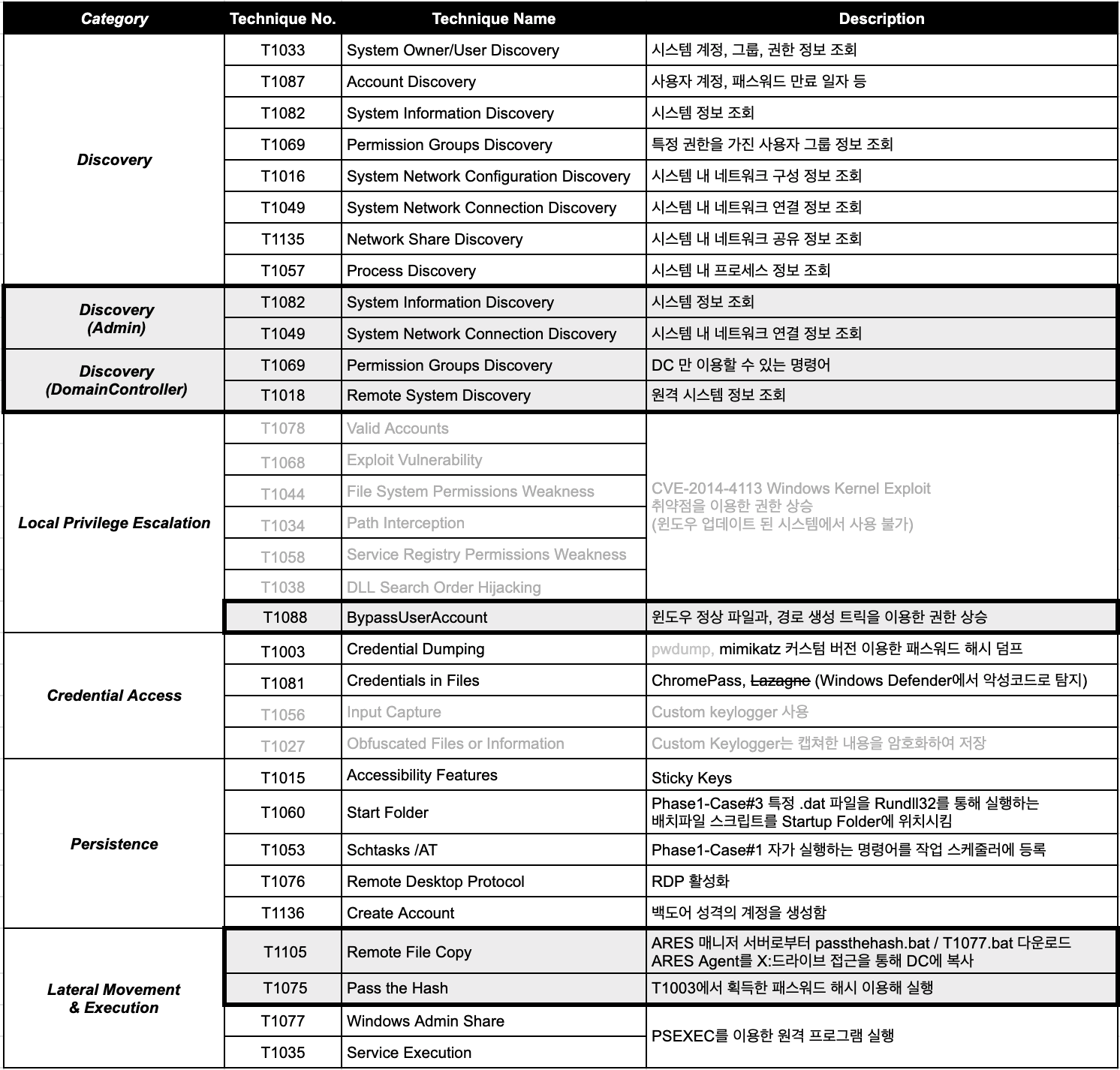
Image - Example of the Attack Techniques used in CHEIRON from the APT3 2nd Attack Stage
The Attack scenario example is listed below. This scenario was not tested using Metasploit or another platform, but was done with CHEIRON’s server-agent platform
- [TARGET A] At the same time as collecting information, acquiring the B System’s authentication value via a connected A System, applying the T1003 Credential Dumping technique
- [ATTACKER] Using the B System’s authentication hash, the attacker acquires the vulnerable password.
- [ATTACKER] Using the collected hash value, the attacker generates a batch file to execute a Pass the Hash attack on TARGET A.
- [ATTACKER] Using the vulnerable password, the T1035 Service Execution technique is executed to run the malignant file in Target B, and generates a batch file to register the Run Key
- [TARGET A] Using the batch file received from the server, the attacker executes a Pass the Hash attack and copies the running file into a shared folder.
- [TARGET A] The batch file received from the server is run in TARGET B.
- [TARGET B] The malignant file is installed, and the attacker sends the information received from the server.
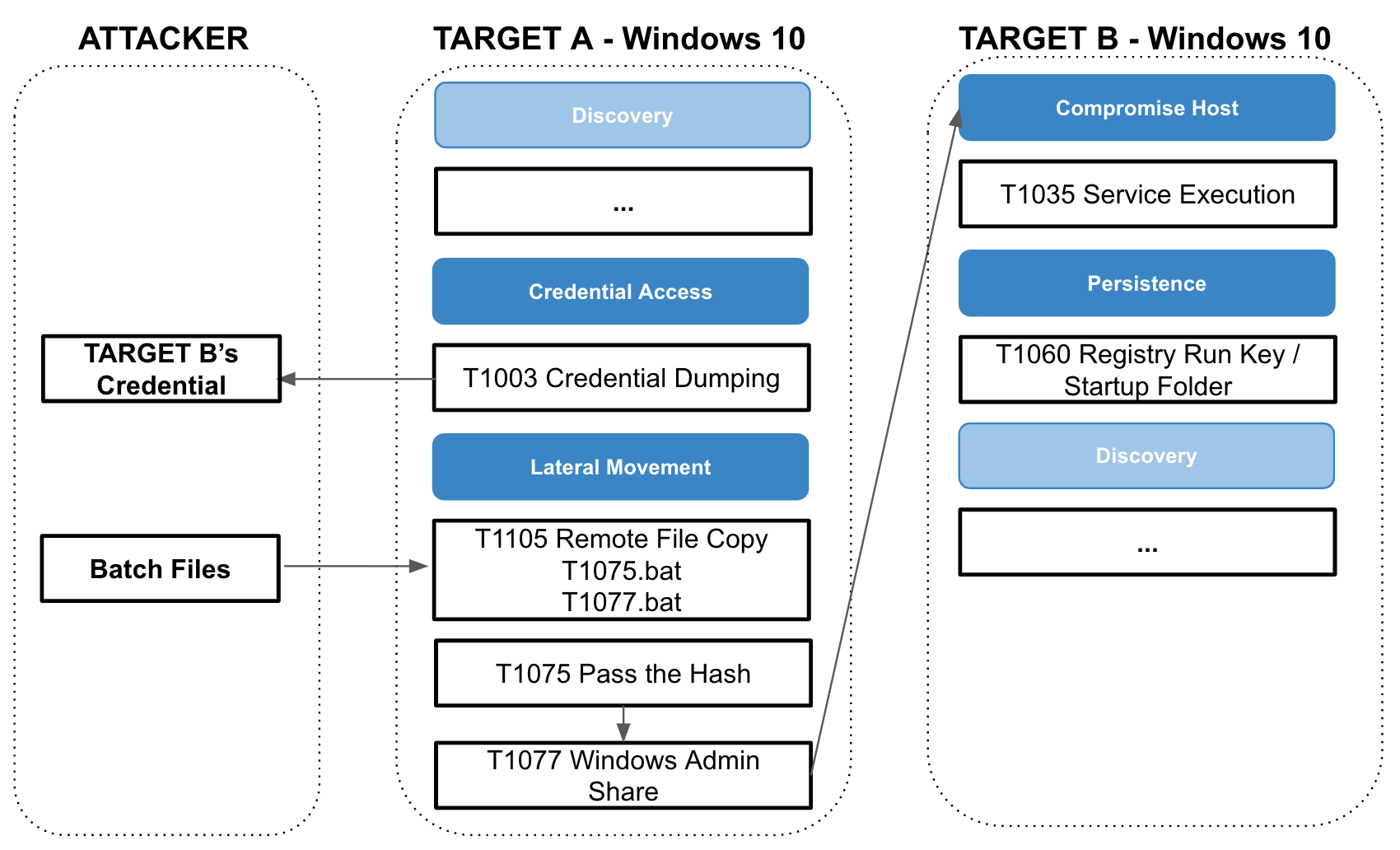
Image - CHEIRON Attack Scenario
The above scenario is a reproduction of Lateral Movement using CHEIRON. A detailed explanation of CHEIRON can be found at APT Simulator and CHEIRON Introduction. An identical blog post in English can be found and read if preferred.
Additional Resources
- [2017, September] APT3 Adversary Emulation Plan - PDF
- [2017, September] APT3 Adversary Emulation Field Manual - Excel
- [2015, June] Operation Clandestine Wolf – Adobe Flash Zero-Day in APT3 Phishing Campaign
- [2014, November] Operation Double Tap
- [2014, June] Clandestine Fox