In this post, the APT Simulator will be introduced, and the Advanced Attack Simulator, CHEIRON, the implementation technology currently in development at SOMMA, will be shared. Partner to this is an introduction to how we implemented the MITRE ATT&CK Matrix into CHEIRON, and how it is currently in use.
APT Simulator
1. Background
What are and why were APT simulators, that first began appearing around the end of 2017 and have grown ever since then, developed (2018.09 The Rise of Adversary Emulation)? In my opinion, there are two simple reasons that do not have to do with actions taken against malignant code, but rather strategies against APT groups, and those are: 1. TTP Testing Based on The Cyber Kill Chain and 2. The EPP to EDR Demand Shift.
1.1. TTP Testing Based on The Cyber Kill Chain
For many people, speaking of an attack framework brings to memory Metasploit. However, Metasploit has flaws that hinder it from successfully reproducing every stage that occurs in an APT attack. Looking at the Kill Chain (pictured below), these flaws are especially prevalent as Metasploit struggles to reproduce and execute the final two steps, taken once the malware has been installed and begins sending commands and taking control. In other words, though Metasploit is sufficiently useful in simulating the initial stages of infiltration by an attacker, it struggles in the later post-infiltration stages, where an APT simulator is more useful. Of course, it bears mentioning that APT simulators cannot reproduce every attack technique out there. Detailed information can be found in APT Simulator Types.

Image - Cyber Kill Chain 7 Steps Wikipedia
1.2. The EPP -> EDR Demand Shift
EPP (Endpoint Protection Platform, can think of the traditional vaccine platform) focuses primarily on detection by means of the signature found with the malignant code’s hash or static signature. This type of detection has weaknesses that are severely vulnerable to malignant code. Additionally, many APT attack groups do not immediately initiate another malicious attack; instead, they often stake out after grabbing control. A perhaps even greater weakness is that the number of ‘Living off the Land’ attacks, those using only normal tools, are increasing in number. In these attacks, after the installation of malignant code, the attacks often use primarily internal Windows tools, such that it is incredibly difficult to detect them via EPP. From the weakness of EPP, grew a need and a subsequent demand for both behavior-based detection products, namely EDP (Endpoint Detection and Response), and testing tools to help detect attacks employing normal tools. As the need and demand for the latter grew, so did the development for APT simulators beginning in about 2018.
2. APT Simulator Types
Other names that ‘APT Simulator’ goes by include Adversary Emulator, Red Team Automation, and Breach and Attack Simulation (BAS). My decision for selecting ‘APT Simulator’ out of the several terms available is because it appears to be the easiest to understand. In America, the term ‘Adversary Emulator’ is often used, but, to us, for some unknown reason, it feels unfamiliar. Regardless, these types of terms that all fit into the same category or group all reference ways in which the tools used by attack groups can be reproduced and tested, providing help especially to Red/Purple Teams. Based on the APT Simulator List released May 17 2019, some of the leading ones are CALDERA, ATOMIC test by Red Canary, and the open source metta by Uber, the functions of each of which will be explained further in detail. (In only a few months it appears that the number of such simulators has increased tremendously. Regretfully, there does not appear to be such a South Korean product on the list…perhaps SOMMA’s CHEIRON is the first?^^;)’)
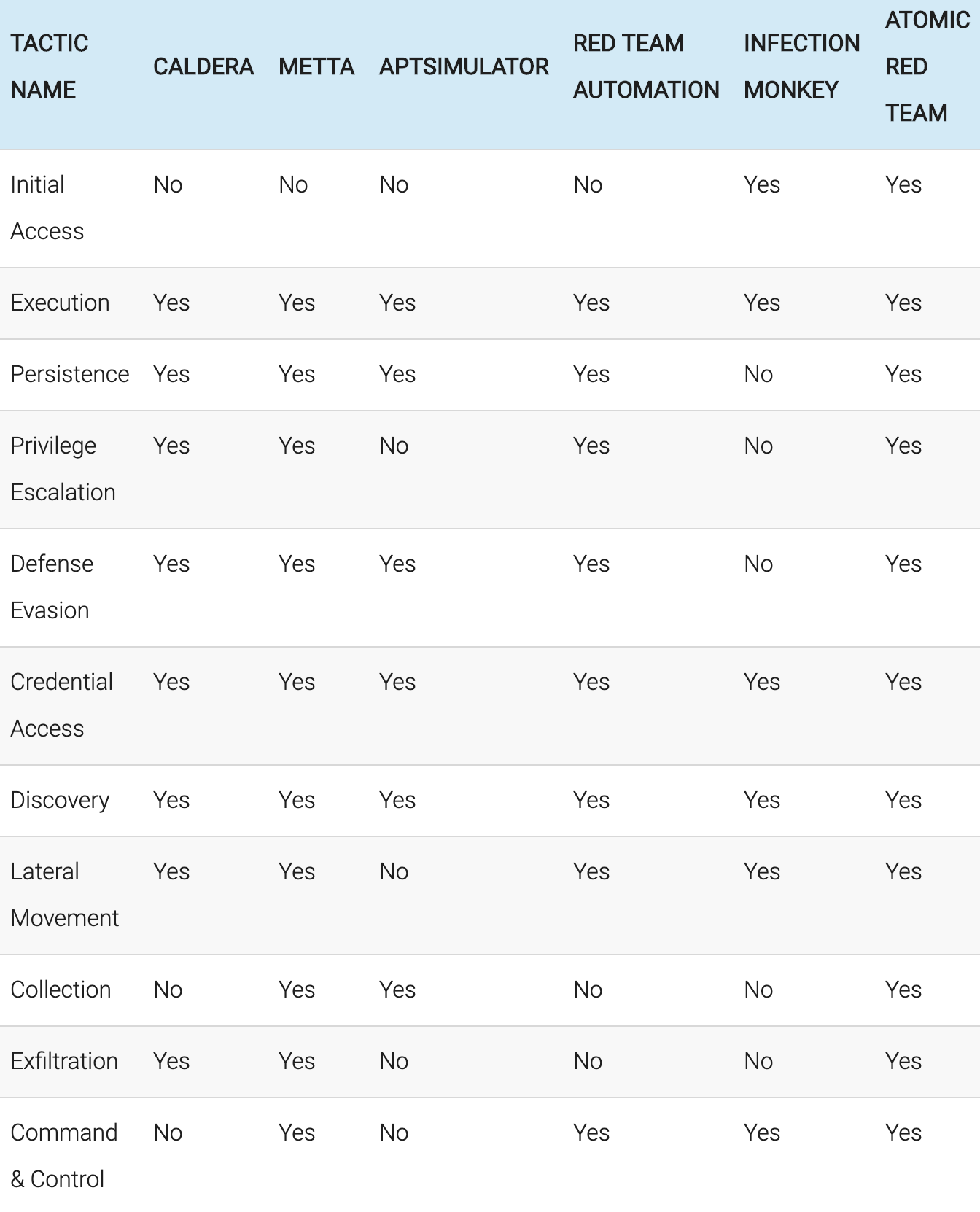
Image - Simulator Comparison by Tactics
2.1 CALDERA
CALDERA is one of the first APT simulators developed by MITRE™ and is one of the most well-known such systems. Its research (Paper) began in 2016 and it is one of the easiest examples to begin understanding APT simulators. However, as much as it is one of the first versions, the MITRE ATT&CK Matrix is not integrated with it, and as RAT, performing malignant actions, is already installed, it will be difficult to to install a new action program. The development environment is the following…
- agent: windows 7 64 bit (python.exe) github-agent
- crater(RAT): C# github-crater
- server: aiohttp + mongo (github-server)
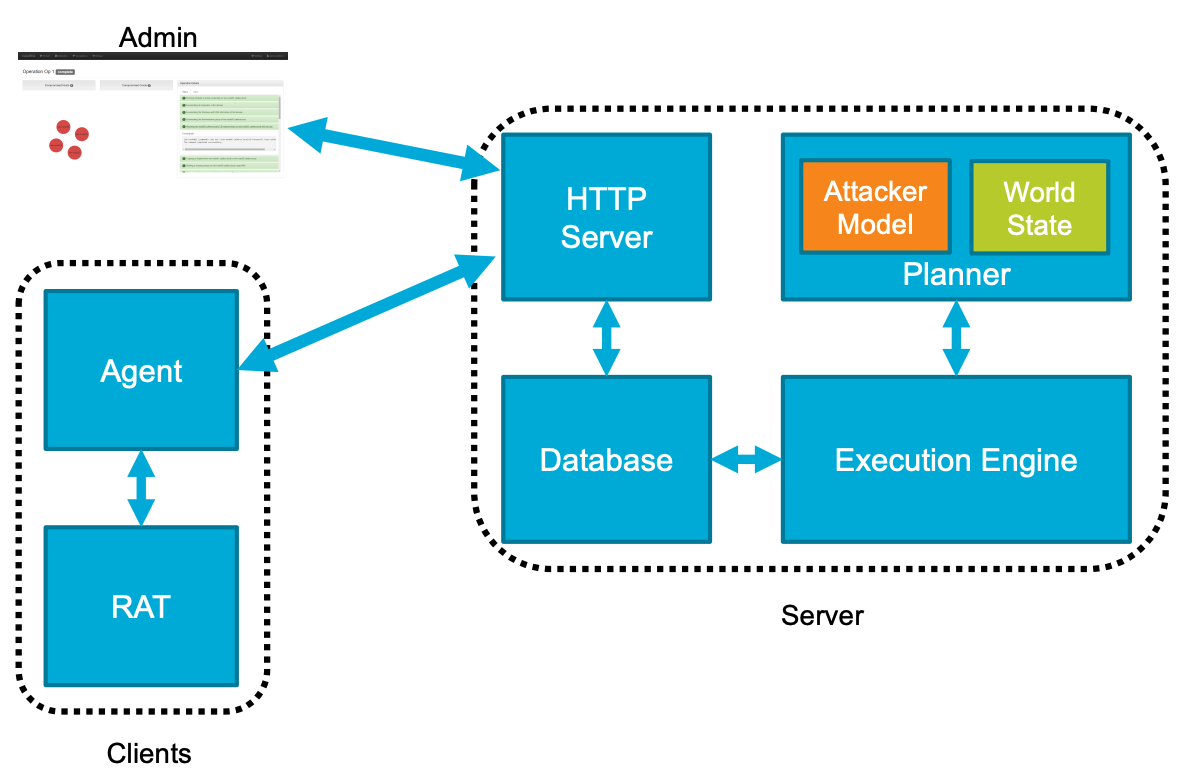
Image - CALDERA System Map
2.2 ATOMIC™ test / Atomic Red Team
ATOMIC™ test is developed by Red Canary and, based off the MITRE ATT&CK Technique standard, the data is encoded in YAML type. The work is parsed, then the program runs off the execution framework, which supports powershell, ruby, and python. The user selects the framework that they want and runs the YAML data. It has the most publicly available technique file data and supports Windows, Mac, and Linux. Moreover, Carbon Black, one of the EDR products, utilizes collection sensors to generate detection rules, supporting IBM SIEM’s QRadar tool’s detection rules. Through the Webinar, a variety of information is additionally shared, including Defense Evasion and Lateral Movement.
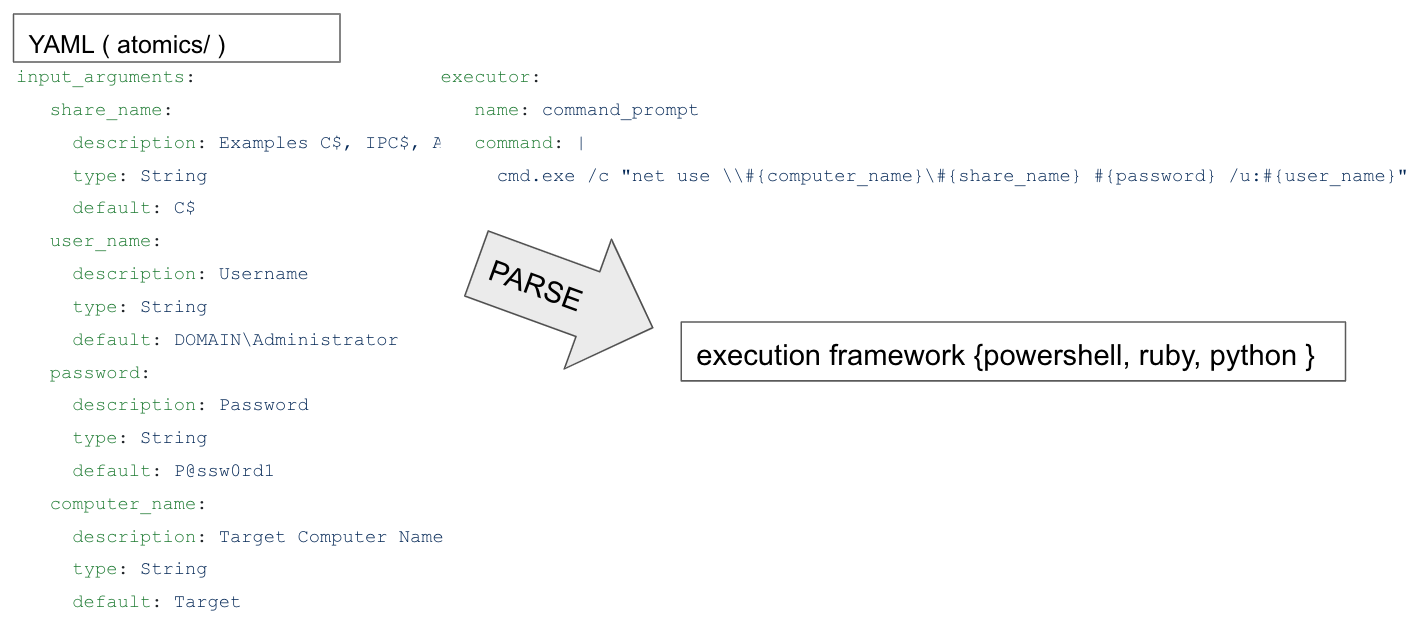
*Image- Red Canary’s ATOMIC testing system’s structure
2.3 UBER metta
Well known for its car servicing application, UBER has among one of its many open source projects a product called ‘metta’. It was developed using Redis/Celery, python, and vagrant, and, of course, the data is encoded in YAML, following MITRE ATT&CK’s standards in ‘Tactics.’ The structure is as follows: 1. Parse a YAML file written based on a Purple Team scenario 2. Run Vagrant 3. Run the Virtual Machine (VM) that is running the desired Operating System (OS). Its greatest advantage is that it is using vagrant. Using this software as a testing bed of sorts, even Python can be used to conveniently test a variety of scenarios.
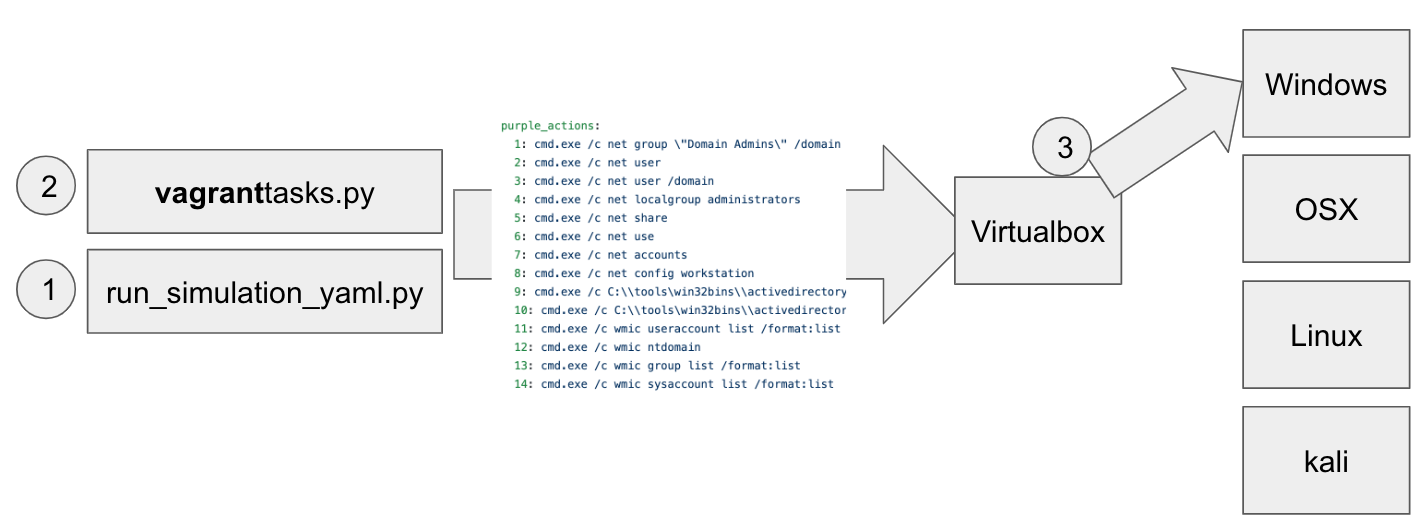
Image - UBER’s metta system structure
CHEIRON
Having said all that, should we know take a look at CHEIRON? CHEIRON is the APT simulator currently in development by SOMMA’s intelligence team. There are several important points that were kept in mind while developing CHEIRON. Similar to CALDERA, the APT simulator can be run in either a server-agent or a single local server form. Supporting both structures means that the most amount of attack scenaros possible can be tested. That is to say, CHEIRON Agent supports both running independently and running more passively, receiving orders from the server. Additional planning has gone in such that the data that supports these two structures can be used in as many formats as possible. Another consideration was supporting a wide variety of simulations: reproducing single techniques, simulating an attack group’s signature attack method, and testing with a scenario as a base (the running data formats will be explained in more detail below). Finally, consideration went into live attack scenarios under the server-agent structure, making the agent as passive and as easy to install as possible.
1. System Structure
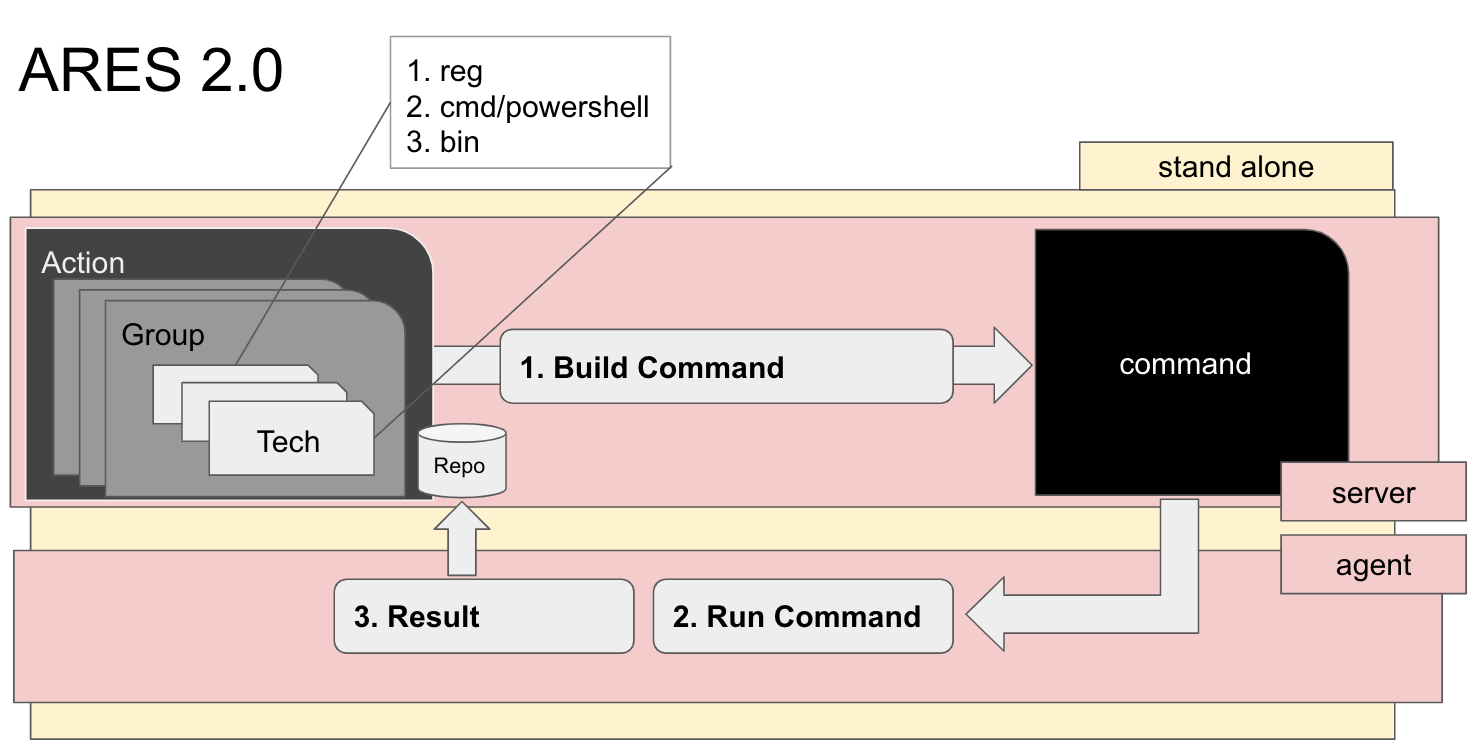
Image - SOMMA CHEIRON’s structure
CHEIRON’ server-agent structure was constructed in a ‘falling’ method using the following elements…
- CHEIRONagent: retrieves and runs commands from CHEIRONmgr
- CHEIRONmgr: managing each run’s data (action, group, technique) and agent
- CHEIRONweb : Web UI supporting the CHEIRONmgr
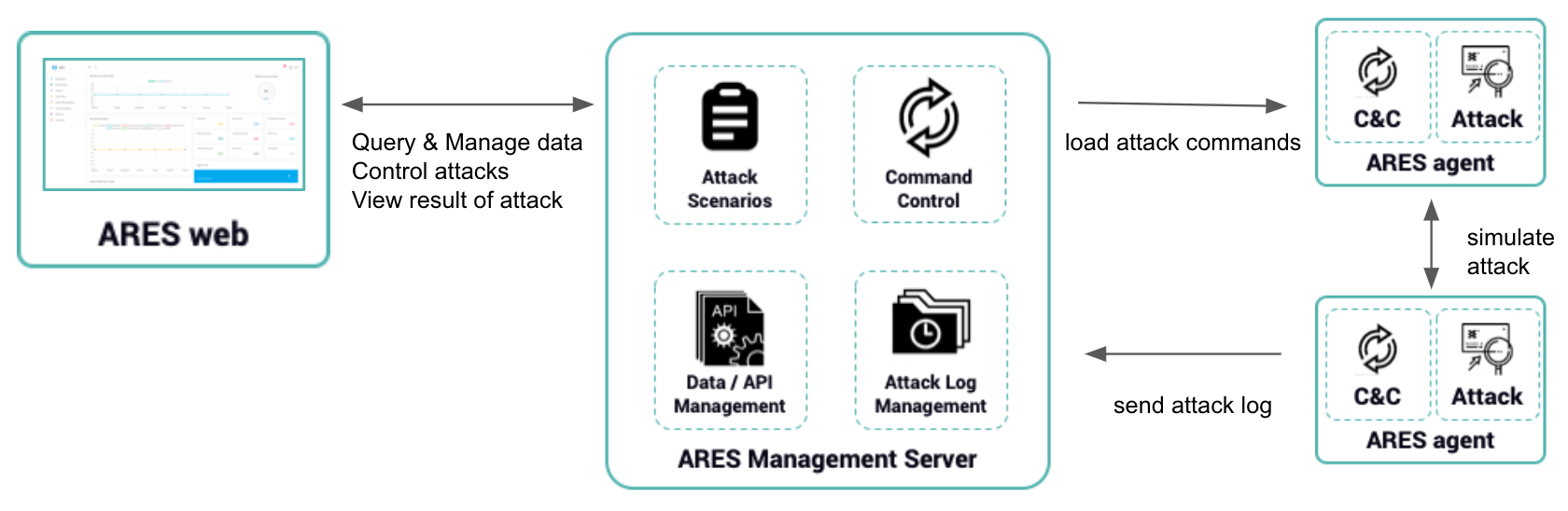
Image- SOMMA CHEIRON’s server-agent structure
The technology stack composing CHEIRON is as follows.
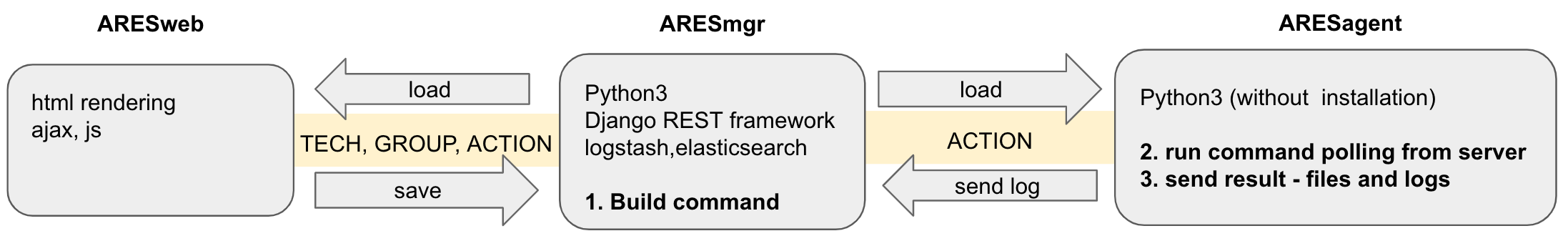
Image - Technology stack composing SOMMA CHEIRON
2. Running Data Format
The data dedicated to creating the running commands is divided into Action/Group/Technique. Technique is given the MITRE technique number Txxxx. It is built for collecting generation and execution of commands. It defines the OS platform systems, executors (powershell, binary, registry, CMD), and execution factors. Group is given the MITRE group number Gxxxxx. It collects techniques and operations based on the group, providing its most effective use in the comparison and understanding of different group’s signature attack techniques. Action does not refer to individual techniques or groups’ tools and techniques; instead, it refers to the combination of individual techniques and groups’ tools and techniques that can be run as actions as a form of simulated testing. It can be used in the server-agent structure with an agent identifier (ip, port), and can also be run at particular times.
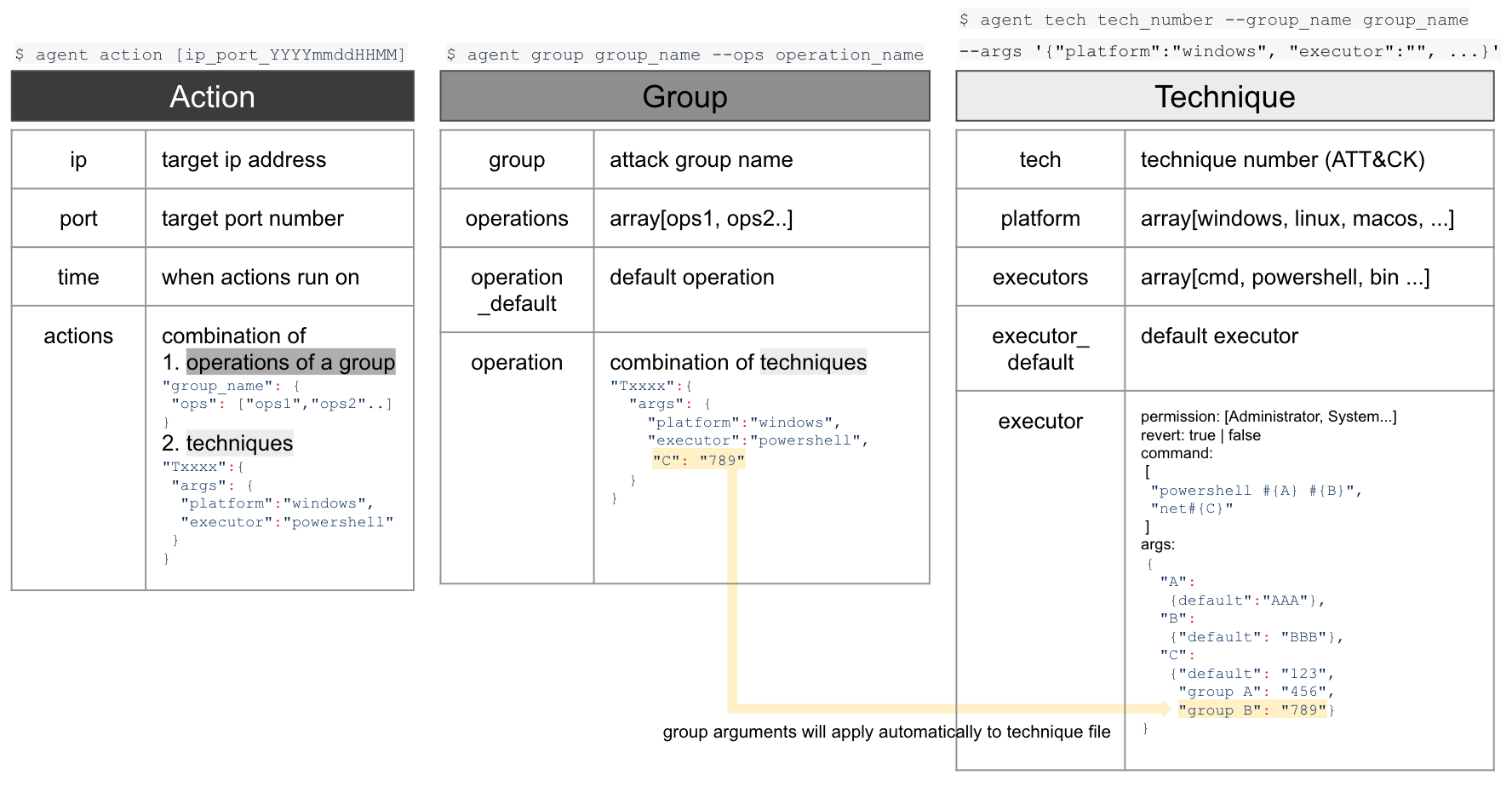
Image - SOMMA CHEIRON’s system’s structure
3. What can be done with CHEIRON?
- Overcome the limits of Metasploit, PowerSploit, and other tools
- Besides detecting malignant code, can be useful in testing whether such attacks’ techniques are detected by the vaccine
- Of course, can be a good tool for creating detection rules or logging other artifacts from attack techniques
- When testing an attack scenario, can simulate with a joining of a variety of attacks
An example of using CHEIRON to test a scenario can be found by referring to APT3 attack and analysis simulation using CHEIRON. Please email support@somma.kr with any questions :)